Rayan Nik Tajhiz Company
Privileged Account Management provides conditions for organizations to secure their applications and infrastructure and maintain the confidentiality of valuable data and critical infrastructure well.
Privileged Account Management (PAM)
Privileged Account Management provides conditions for organizations to secure their applications and infrastructure and maintain the confidentiality of valuable data and critical infrastructure well.
High-level user accounts are favorite targets for cybercriminals. These users have special permissions in the system that allow them to access highly confidential information or change the settings of primary programs and systems.
The PAM product was introduced by NET ARCON as ARCOS and was launched to keep organizations safe from intentional or unintentional incidents through classified access.
Advantages of using the PAM system:
- protection against cybercriminals
- protection against insider attacks
- more efficiency with PAM
- reliable adaptability
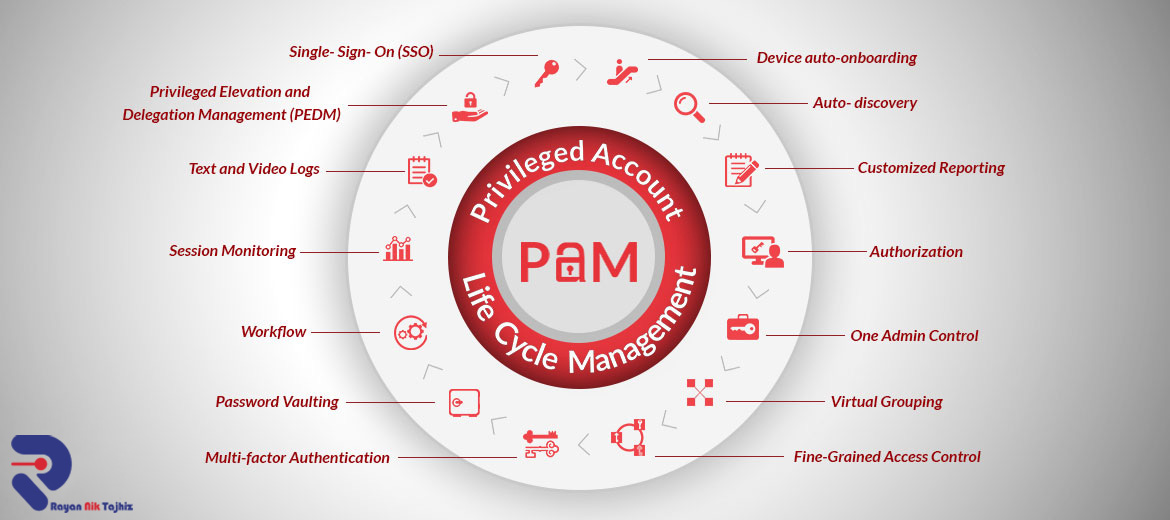
Examples of Privileged Account Management:
- unified authentication–Single Sign On (SSO)
- safe storage of passwords – Vault Password
- Dual-factor Authentication
- One Admin Control
- Smart-Audit-Trail
- SSH Keys management
- Granular Access Control
- Virtual Grouping
- Session Recording
- using Microsoft Active Directory in the authentication process – Bridging AD
- Privileged Elevation & Delegation Management (PEDM)


