Rayan Nik Tajhiz Company

ORACLE VAULT
Oracle Company has provided various products to increase the security of databases. These products include Oracle Database Firewall, Oracle Vault, and TDE (Transparent Data Encryption). These products complement each other to maximize database security controls.
Misusing the account of database users who have high access to information is one of the most common and important methods of stealing and infiltrating databases by hackers. Therefore, the Oracle Vault product, which creates security controls in the database, makes the data safe from unauthorized access.
What is Oracle Vault?
Oracle Vault monitors and controls the access of allowed people. Some people may have a top level of access to the information in the databases according to their organizational roles. However, if the access is uncontrolled and with no restrictions, entering all kinds of viruses and malicious database attacks will occur.
Therefore, with the help of Oracle Wallet, it is possible to limit the access of all users, including database administrators. For example, they cannot access the sensitive information of their colleagues, such as their salary.
Oracle Vault provides powerful security controls to help protect organizations’ data against unauthorized access while complying with regulatory and privacy requirements. These controls can be extended to allow access to sensitive data by senior administrators with special privileges, block insecure paths, and control sensitive database operations using authorization. Data center security can be enhanced through privilege and role analysis. In addition, Oracle Vault transparently secures existing database environments, which eliminate costly and time-consuming application changes.
In Oracle Vault, by using multi-factor access permission, it is possible to prevent unauthorized access of privileged users to application data and control sensitive activities in the database.
To create these restrictions, Oracle Vault uses the Oracle Database Vault Realms protocol, which is called Realms for short. This protocol creates a very limited user environment in the database so that they can perform their regular work activities besides limiting the access of users to all the internal information of the database.

The most important features of Oracle Vault
- Enforcing security rules to monitor activities
- Oversight of sensitive data by the senior manager
- Creating a reliable path for access
- Blocking unsafe routes to data centers
- Internal support for PostgreSQL
- Oracle Database RAC support
- NIC connection to increase traffic throughput
- Collecting SQL traffic on the host machine
- LDAP/Active Directory authentication
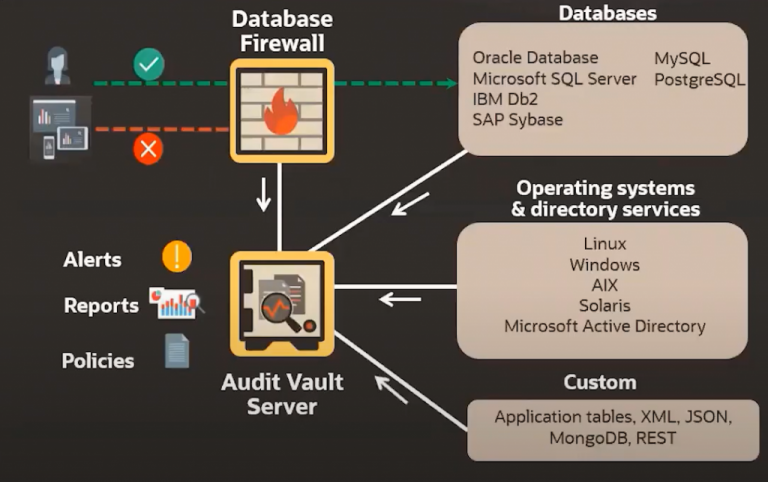
Features of Oracle Vault for managers
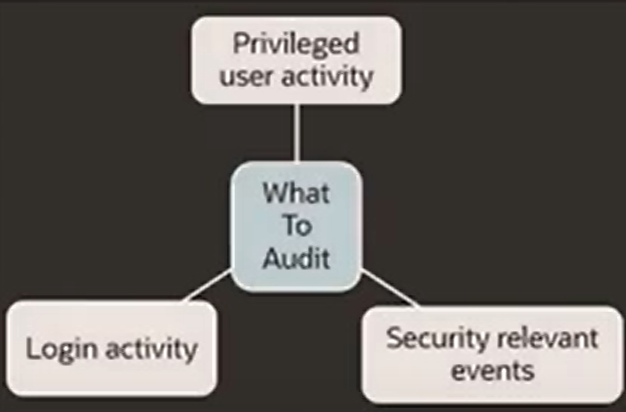
- Managing the access of senior managers regarding user activity
- Controlling relevant events regarding database security
- Checking the data center’s entries
- Following up on unusual activities
- Dealing with failed logins according to their reasons
- Oracle Key Vault management and implementation
- Securing, sharing, and managing keys and confidential information for organizations
- Scheduling automatic backups in a remote location
- Providing reports and alerts
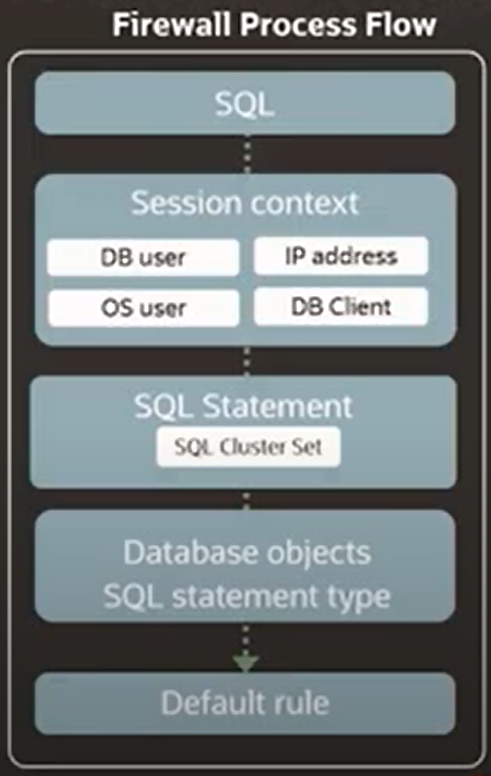
How to monitor incoming and outgoing traffic for access control?
SQL Server uses locks to maintain data integrity for reading and writing so that only one process has control over the data at a time. When locks are held for a long time, they cause blocking, meaning that one process must wait for another process to finish and release the lock before the other process can continue. This structure can provide us with the following features:
- Extensive report of SQL activities
- Data traffic disruption report
- Monitoring and warning about unauthorized traffic
- Access is determined based on application prerequisites
Reporting structure of Oracle Wallet
The reporting structure, because of the ability to adjust and plan, can be recorded to report logs of all activities and operations that are performed on the databases or even performed by the database itself, and the results will be saved as a separate file from the main database.
In Transaction Logs, there is data in the databases in every transaction or exchange You can extract the information needed to restore the changes to the original state from these Transaction Logs before doing the transactions.
When a transaction is to be done in a database, the current state before the transaction of the database is stored in Transaction Logs, and if needed, you can undo your information and data to the previous state.
Oracle vault receives the desired data from the database and according to the logs, it can control and monitor the traffic and finally provide a report or warning about suspicious cases in the database. This unique feature has made organizations identify problems in the shortest possible time.
In most practical structures, data security is a key benefit, and Oracle Audit Vault offers such a benefit. Software like Oracle E-Business Suite or SAP must be used to tap into this system. While the reporting tables may create duplicate reports, Oracle Vault gives an assurance regarding all the data and the reporting process that there is no need to copy or repeat the reports unnecessarily.
SAP can record all successful and unsuccessful user logins. Oracle Audit Vault collects information about accesses and logins that have been made. Audit Vault will alert and report the event if this information is deleted or updated.
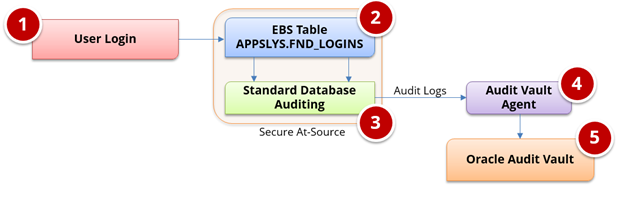
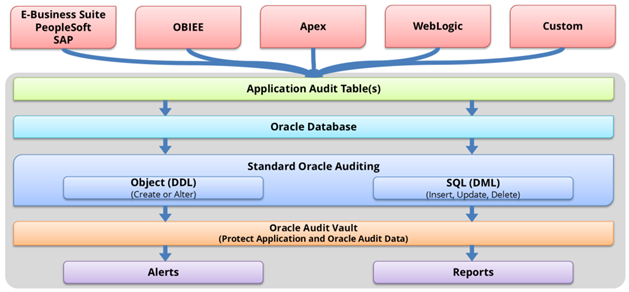
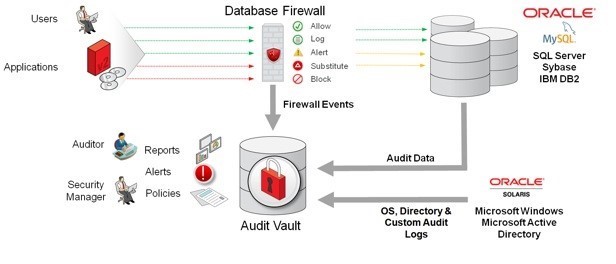
Conclusion
Oracle Audit Vault and database firewall examine database traffic and take necessary actions to block threats, improve data aggregation for auditing data centers, and monitor activities.
Preventive controls to block users and administrators of high-access databases and also prevent their access to sensitive database data have made this structure reach a prominent position among large organizations.

