Rayan Nik Tajhiz Company
What is one-time password (OTP) service? Explained together with applications and authentication mechanism

What is one-time password (OTP) service?
In Iran, application of one-time password (OTP) has been regulated as required for bank transactions since June 2019. As of present, you need an OTP before you can pay for an online service or shop online at any amount beyond 1,000,000 IRR.
But what is an OTP? Technically speaking, an OTP is a one-time-usable string of numbers or characters that serves as your password to sign into an online system or perform a financial transaction while authenticating your identity in such a way to prevent hackers from accessing your password.
Records of compromised passwords and their utilization for authentication by unauthorized persons on online services have increased substantially, especially during the recent past. An OTP service generates one-time passwords to avoid reoccurrence of this unpleasant experience to users. When an OTP is submitted to log into a system or use a service, it is immediately expired upon use, making it no longer usable for the same purpose. Put simply, OTP is a one-time encryption system that prevents from password compromise and intrusions by unauthorized persons with the help of the compromised password.
Authentication mechanism; securing the identity verification process
When a request for OTP is submitted during online shopping or using an online service, virtual key storage applications become deactivated. That is, once the OTP was sent, such applications redirect the OTP to the service/shop owner (i.e., you). Traditional authentication processes were based on static passwords, while OTP exhibits a much better performance against cyberattacks as it remains valid for only one try within 1 or 2 minutes of its generation. Moreover, with an OTP, if you use an identical password for each device on each day, other passwords remain secure if one of them is hacked in some way.
User authentication; the commonest application of OTP
While such tricks as virtual keyboard or second pin rendered ineffective in securing the user’s information, OTP could make the data theft impossible. You probably have some experience of working with OTP when placing bank/financial transactions. OTP is a security solution for authenticating the customers before finalizing a bank transaction or letting the user log into an electronic system in an attempt to prevent wrong authentication of unauthorized persons.
As a part of the user experience as he/she shops online or uses an online service on particular websites (e.g., cryptocurrency exchanges or digital products e-shops), OTP encryption service is utilized to authenticate the users through their cell numbers. An example of this process is when you sign up on a website and an OTP is sent to your mobile phone via SMS.
OTP: Cons and Pros
Regardless of the extent to which a developer takes security measures, no one can reasonably guarantee exactly complete control over user data security. In an atmosphere where every company is seeking to promote their own OTP technology as the most advanced player in the market, the OTP services will be more vulnerable when they become available to third parties. The following table presents a summary of the Cons and Pros of the OTP technology.
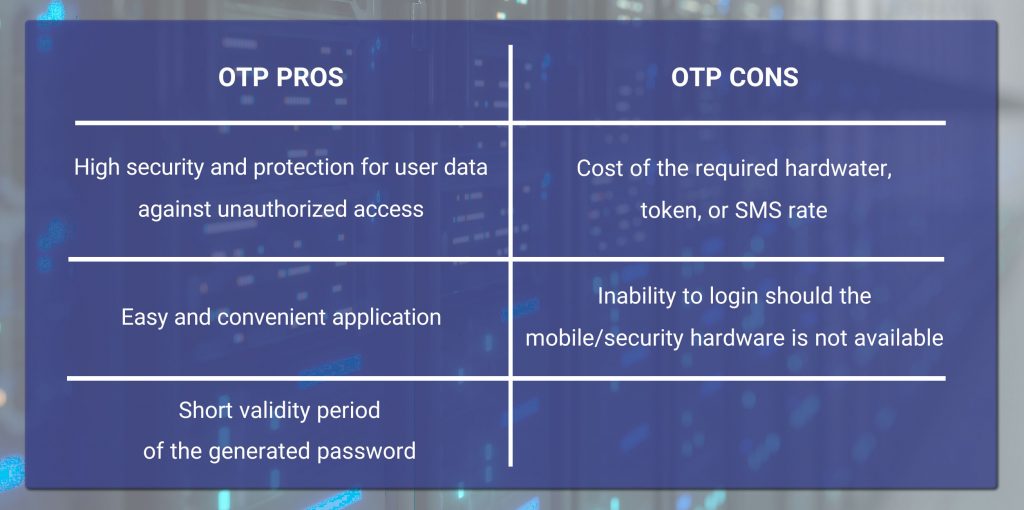
Despite the security and safety brought about to users by the OTPs, application of this technology may render challenging in particular conditions. For instance, when the hardware token or mobile app is not within your reach, you will end up with no way to sign in. Altogether, however, advantages of an OTP service dominate its disadvantages.
Various types of OTP: HOTP, OTP, and TOTP
OTPs come in different types, each of which going through a different method of user authentication. These types mainly differ in the method of generating the password. Indeed, with an OTP system, the user can be authenticated via either of three methods, namely HOTP (where the “H” stands for Hash-based Message Authentication Code (HMAC)), OTP, and TOTP (where “T” stands for time-based).
OTP method
To generate an OTP, one needs to inputs, namely a seed and a moving factor. The seed is a constant numerical value that is generated on the OTP server as the user logs on. The moving factor, on the other hand, is a dynamic value. This code is generated by means of standard hash algorithms. Decrypting a hashed password is practically impossible as the hacker has no way but to go through reverse computing to achieve the required initial data for hacking – a practically impossible mission to accomplish. You can use OTP generation applications to obtain an OTP.
HOTP method; event-based OTP
The letter H in HOTP refers to the hash-based nature of this method. Whenever a HOTP code is requested, the moving factor is updated based on a counter, and this password remains valid until a new code is requested.
TOTP method; time-based OTP
The letter T in TOTP refers to time – this is a time-based OTP. Here again a constant seed is combined with a moving factor that is herein updated by time. These OTPs remain valid for usually no more than 1 or 2 minutes, after which they become invalid.
Which type of OTP is better?
Time-based OTP (TOTP) represents the newest generation of encryption. Thanks to its time-limited nature, the TOTP provides for a higher security level. Albeit, this limitation may push the user toward facing particular challenges, and this is why the HOTP method is usually more user-friendly as it uses a hash limitation instead of time limitation. In the meantime, HOTP is less secure than TOTP and can be a subject of a brute force cyberattack.
Methods of presenting OTP
How to activate OTP?
Various methods of using OTP have been developed. Some systems make use of special security symbols. You can also use customized applications to obtain your OTP on demand. The security systems where OTP is generated on a server send the generated code to the user through a particular channel such as SMS. You can also obtain an OTP via a token, mobile notification, or online channels.
Application of voice or text message on mobile phone; text-to-speech conversion
Text messages sent as an OTP are used through text-to-speech conversion. That is, the password is sent to the user through particular applications, such as a voice call. For an OTP verification system to work, there is no necessity of network connection or Internet access.
Application of online methods; the simplest approach to OTP
In addition to SMS, you can obtain an OTP online with the help of random data such as letters, images, or numbers. This is the simplest approach to OTP.
Application of OTP token; a special hardware to generate OTP
A common approach to obtaining a temporary second pin code is to use an OTP token. But what is an OTP token? It is a hardware tool that utilizes mathematical algorithms to generate OTP. Continuing with this article, we explain how to activate an OTP token.
How to obtain an OTP with an OTP token for our bank transactions?
Once you obtained the OTP token as a hardware, you can input your financial information on the payment page and then keep your token in front of the page to scan the required data. The token will then redisplay the data to you for the sake of confirmation. Once you confirm the payment information, a digital signature is generated, by which you can log into the portal and finalize the bank transaction.
Rayan Nik Tajhiz; a vendor of token and OTP services
Password generation devices (i.e., tokens) ease the process of obtaining OTPs for online services. By offering versatile OTP services, Rayan Nik Tajhiz helps you easily obtain your OTP on your token whenever you need one. If you feel a need for any guidance and consultancy on OTP services or encountering any problem in obtaining OTP, please do not hesitate to contact our experts at Rayan Nik Tajhiz via phone +98 21 88209219 Ext. 222 to enjoy our free yet specialty support.

