Rayan nik tajhiz company

F5 Service Features
The F5 company’s principal expertise is designing and manufacturing network optimization equipment and increasing equipment efficiency using ADN technology. This company began its activity by introducing F5 Firewall and F5 Network Management equipment.
By providing various solutions and carrying out continuous planning to optimize applications based on network and security and by creating a proper performance on server devices and storage equipment, F5 company has taken a big step towards security and network management development and caused a dramatic evolution.
F5 Firewall features
The data protection method in case of data loss is making a backup of those data so that they can be used for data recovery when needed. The physical storage location of these backup files should be somewhere separate from the original data storage location. As a result, this information should be transferred through the WAN network, and in transferring data through the WAN, the transfer speed and spare capacity of this process will reduce your efficiency. The F5 company has solved these problems with the Application Acceleration Manager service and made this work possible for organizations by using a small amount of capacity and a few processes.
Most of the information of an organization is duplicated. By removing this duplicate data, the amount of information transmitted over WAN lines can be reduced by ten times. This method can reduce the file size by 500 times for Data Type files. The behavior of the TCP protocol reduces the transmission speed in the WAN network, provided that the TCP load can be reduced and managed. Therefore, you can use 100% of the spare capacity and increase the speed of your applications. All these facilities are provided to organizations by F5 equipment in a secure structure.
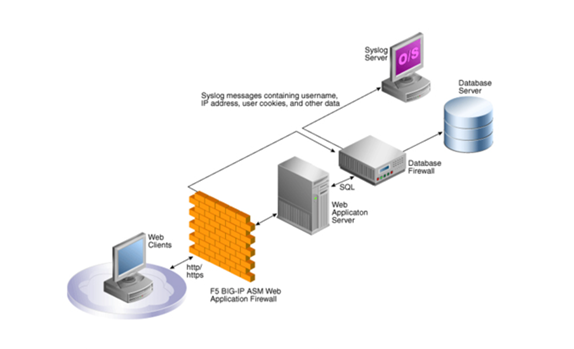
By providing powerful F5 BIG-IP firewall platforms, advanced modules, and central management systems together, f5 company has provided the most comprehensive set of security tools regarding applications in network security. In the following, we discuss the primary features of firewalls of this brand:
1. GMT (Global Traffic Management)
As a solution to balance global data traffic, the Global Traffic Manager improves application accessibility by securing and speeding up the domain name resolution process.
2. LTM (Local Traffic Management)
Local Traffic Manager enables intelligent traffic management for faster application deployment, optimization, load balancing, and data transfer to peripheral networks.
3. AFM (Advanced Firewall Management)
Advanced Firewall Manager is a highly efficient proxy-specific network firewall designed to protect your data environment from incoming threats.
4. APM (Access Policy Management)
Access Policy Manager enables control and monitoring of active people in their practical applications and the network.
5. ASM (Application Security Management)
Application Security Manager secures your practical applications with advanced-level threat protection and location visibility.

6. AAM (Application Accelerator Management)
Application Acceleration Manager speeds up application delivery and controls capacity demand for image data.
7. Secure Web Gateway services
This service enables complete monitoring and control of internal and external traffic, which makes it possible to access employees via the web with no worries.
8. Web Safe
This product provides customer confidence and employee security against various threats in the industry with a highly sophisticated approach to protection against malware and web fraud.
9. SDC (Signal Delivery Controller)
Signaling Delivery Controller’s simple network architecture provides unparalleled scalability and flexibility as a platform for network routing, data load balancing, and network performance.
10. Link Controller
The link controller directs internal and external communications to the best possible link and improves application performance by prioritizing traffic.
11. PEM (Policy Enforcement Management)
With the help of Policy Enforcement Manager, service providers can more easily understand subscriber behavior, formulate more customized service plans, and improve service quality.

